Diaspora- Innovative Solution by zaiTEC Logixs
zaiTEC Logixs have started working with Pakistan Embassy Ireland in 2020. Back then they were managing their entire diaspora operations through excel sheets. After having multiple iterations of requirement gathering zaiTEC was able to make a high-level architecture of their operations and then proposed a Diaspora/Consular Payment Management System that can automate their entire diaspora/consular services including workflow management, appointment booking, standardized receipts, reporting, and data analytics. The end product was deployed in a very short period of time and was well appraised by Pakistan Embassy Ireland and the diaspora. Pakistan Embassy Ireland utilized the system in a meaningful manner and was able to generate different analytics through the system. The following is just a glimpse of analytics and reporting through Diaspora/Consular Payment Management System.

An organized approach at collecting data is extremely important to draw meaningful conclusions.
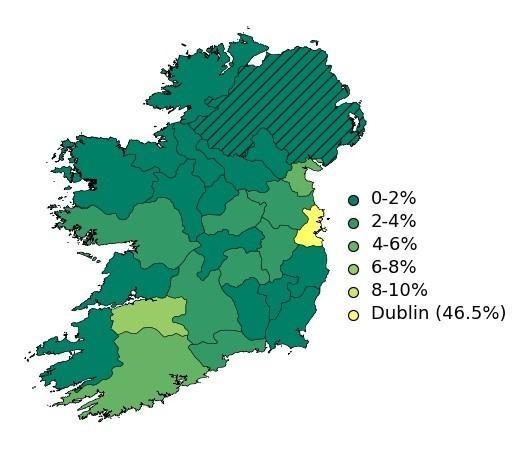
In 2021, we worked on our processes to facilitate the same and answered the question of Diaspora spread in the country
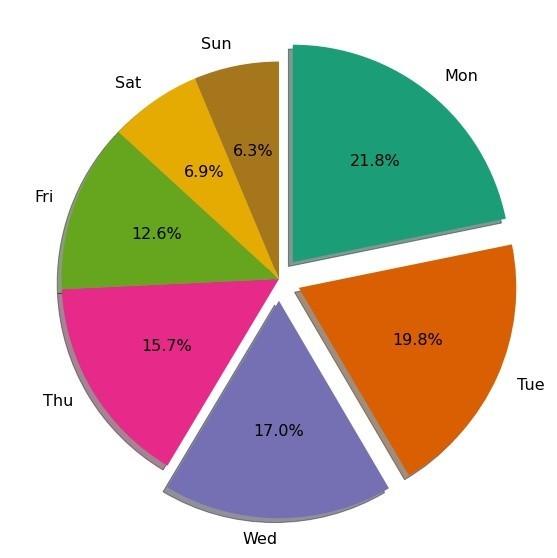
When does our Diaspora usually book their Passport appointments?
Again, conventional wisdom dictates it is done in their free time, esp. weekends. However, data shows that our Diaspora mostly sits down to book appointments on Mondays, Tuesdays & Wednesdays between 10 am-2 pm